OAuth 2.0
Describes how to let users authorize third-party applications to access Optimizely Web Experimentation data using the REST API.
Optimizely Web Experimentation provides the OAuth 2.0 protocol to let users authorize third-party applications to access Optimizely Web Experimentation data with the REST API. It lets any Optimizely customer grant access to an application without sharing their Optimizely username and password. View and revoke applications you have authorized in your account settings.
Optimizely's REST API lets you create and manage Optimizely Web Experimentation projects and experiments and analyze results from other applications. For example, our solutions partners and technology partners use the REST API to:
- Use Optimizely Web Experimentation to A/B test headlines from within WordPress
- Create Optimizely Web Experimentation audiences based on information collected from your Data Management Platform
- Manage Optimizely Web Experimentation projects from an internal system
- Pull results data into an internal dashboard or results widget
- Send email alerts when certain results are achieved
Applications that are built on the REST API (such as technology integrations) can use OAuth to access Optimizely Web Experimentation data on the customer's behalf by putting them through an authorization flow (similar to how you can log into many accounts via your Facebook or Google+ login).
Authorize applications
You can grant trusted third-party applications access to your Optimizely account by logging in via a button that looks like this:

View authorized applications
You can see a list of third-party applications that you have authorized to access your Optimizely data by going directly to the Registered Apps tab in your Account Settings..
Revoke permissions
To de-authorize, a third-party application at any time, simply revoke it from this menu by clicking Revoke Access and confirming your decision. Once you revoke permissions, you can't authorize or re-authorize third-party applications from this menu. To do that, you'll have to go back to the app you want to authorize and go through the authorization process again.
Register applications to use OAuth
To build integrations using Optimizely Web Experimentation's REST API, reference our API Documentation, which covers the endpoints and calls you can use:
If you want to register an application to access the API via OAuth:
- Go to Account Settings > Registered Apps.
- Click Register New Application.
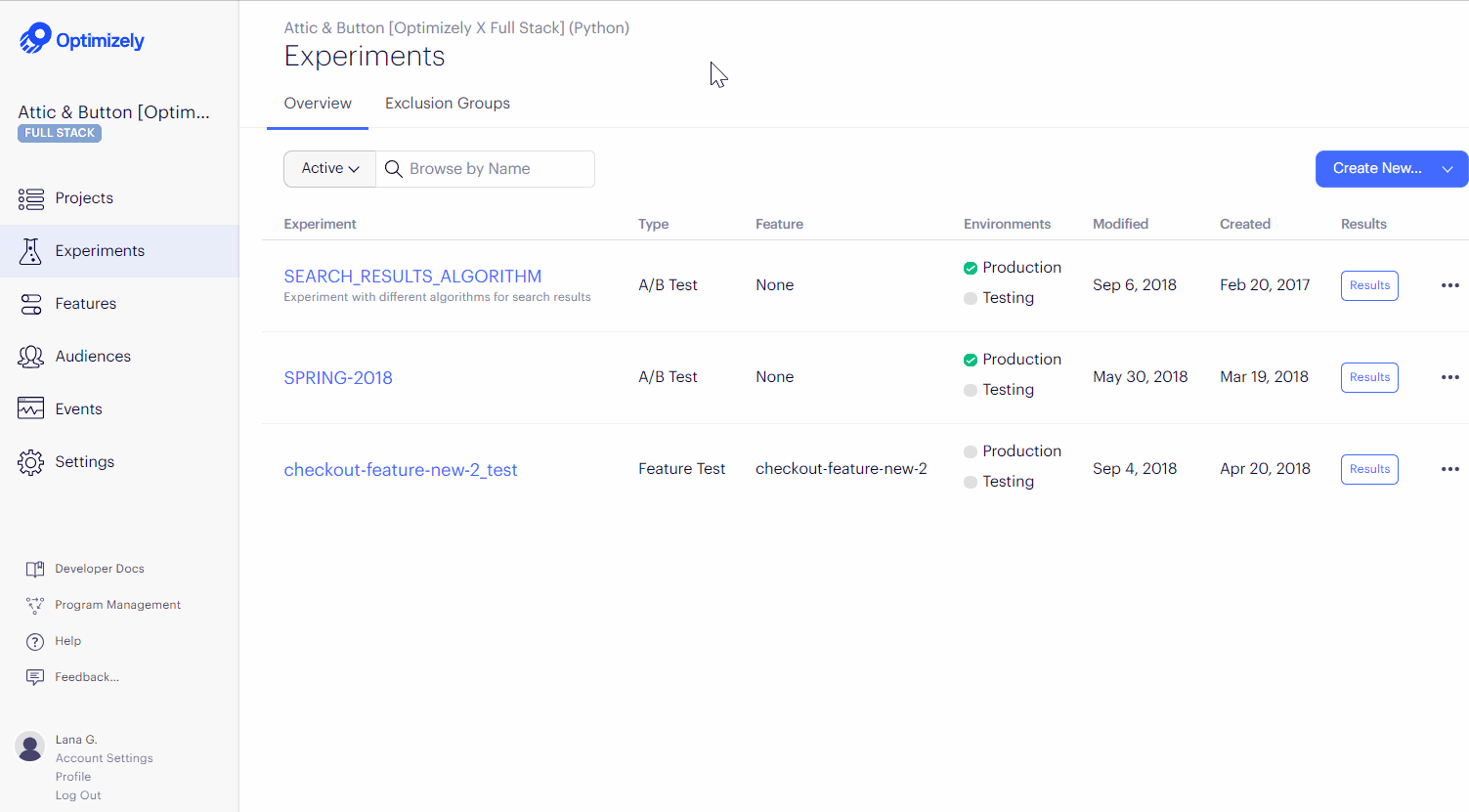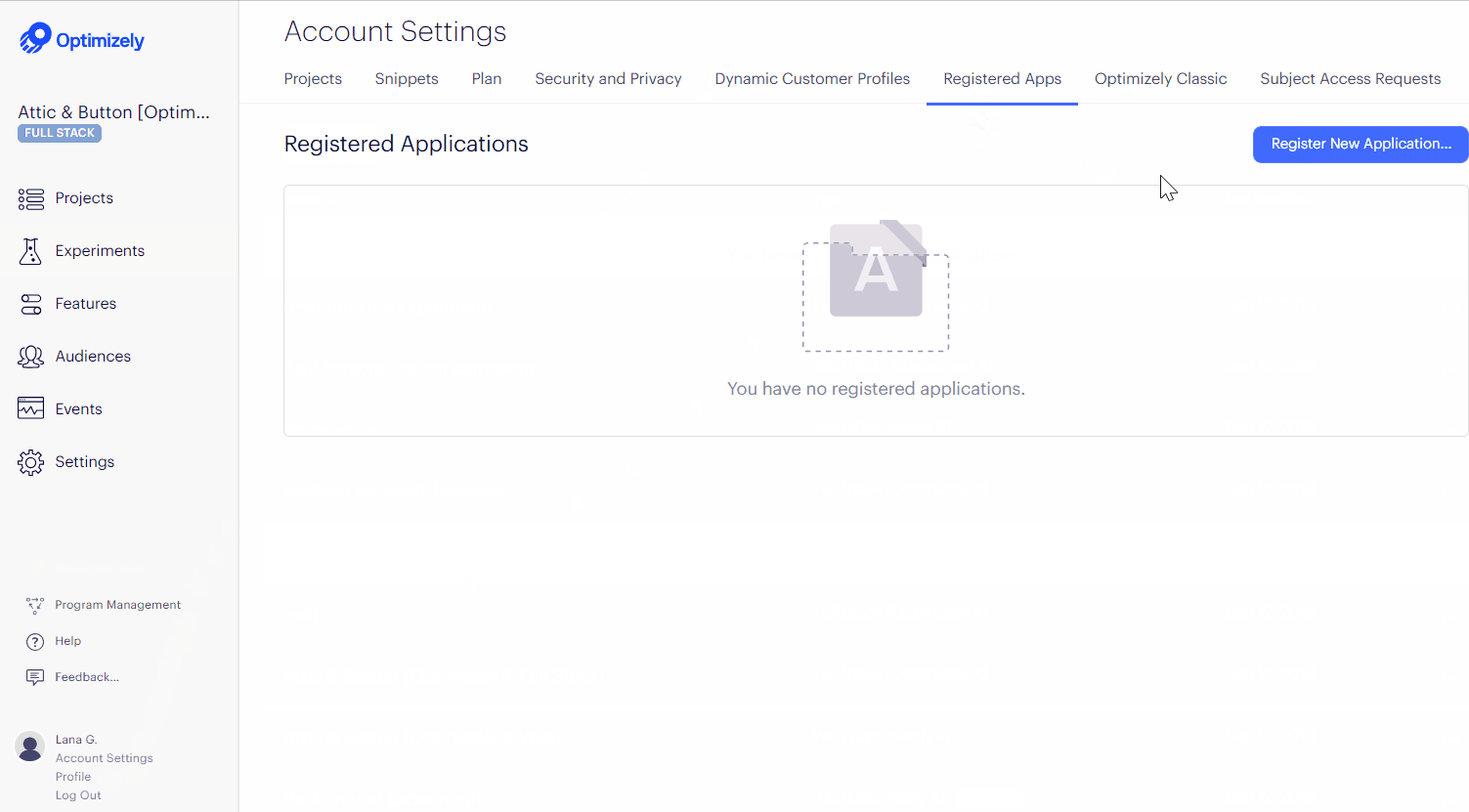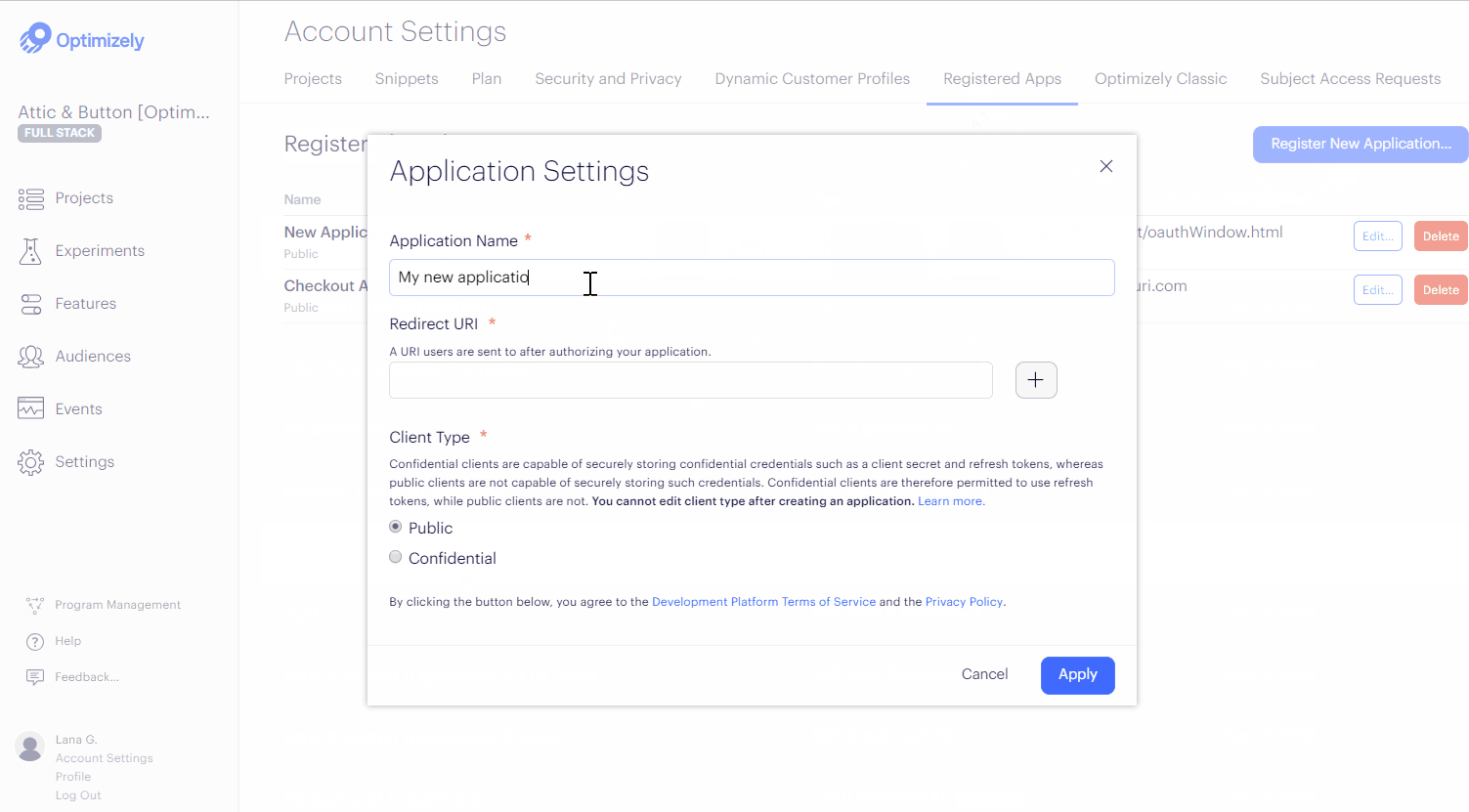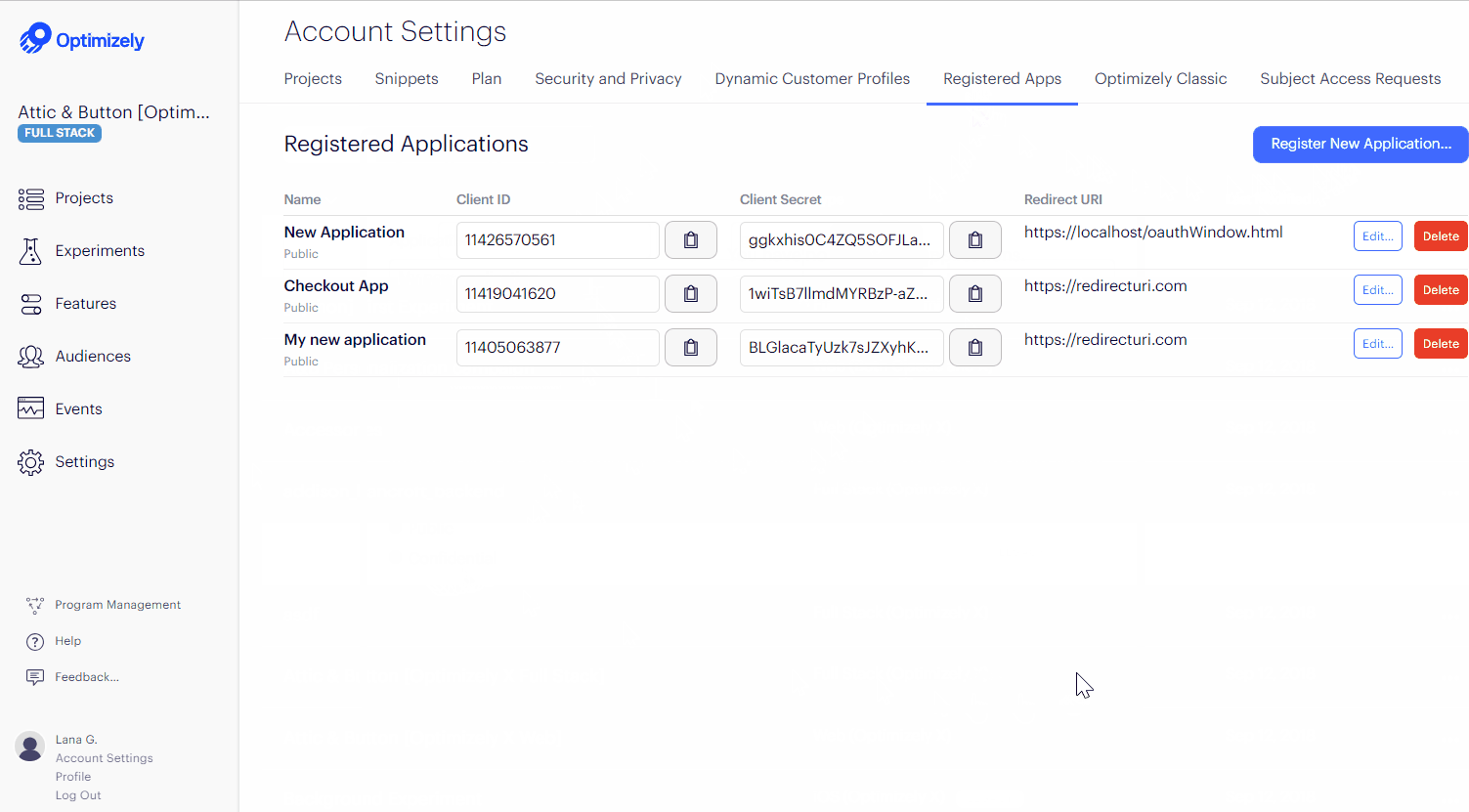
- In the Application Settings window, enter the Application Name and Redirect URI and select a Client Type (Public or Confidential).
- Click Apply.
Build an OAuth 2.0 flow into your application
To build an OAuth 2.0 flow in your application, you will need to complete the following steps:
- Decide which Grant Type is most appropriate for your application.
- Register your application with Optimizely.
- In your application, point customers to Optimizely's authorization URL.
- Process a redirect after the user accepts (or rejects) your application's access.
- Obtain an access token, via an authorization code or refresh token, or via the redirect itself, depending on the authorization flow you're using.
- Authenticate with the REST API using the provided access token.
The sections in this category walk through each of these steps in detail.
If at any point you have questions or need help building out an OAuth 2.0 flow, you can submit a ticket to the developer support team. We'll be happy to help.
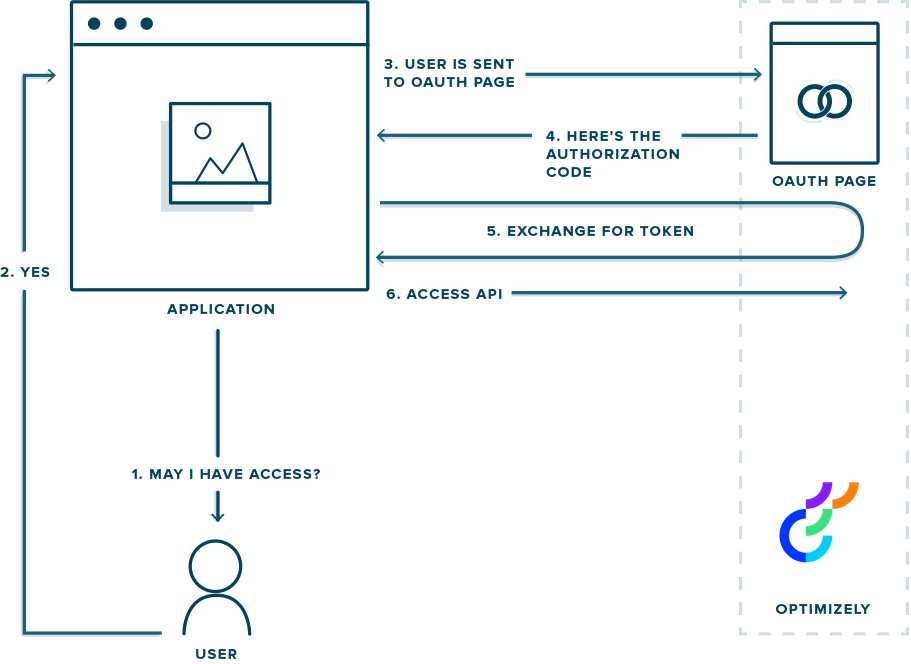
OAuth 2.0 flow
Updated 3 months ago